At this point in our journey through the Raspberry Pi tutorials you will have already encountered certain commands that start with ‘sudo’. In this post we are going to see what ‘sudo’ is and how to use it to run commands with root permissions.
Basically, ‘sudo’ is an application that allows us to run another command with elevated or administrator permissions. It is necessary to prepend it to certain commands so that we can execute them.
But to understand its necessity, let’s briefly see what a user and a super user are, and what role ‘sudo’ plays in all of this.
Users and super users
As we know, one of the strong points of Linux is its security. And any security system is based on good user and permission management, as we will see in the next post in the series.
In Linux we have “normal” users who, generally, have permission to run programs and interact with files in their ‘home’ folder. So, for example, the ‘pi’ user with which we access Raspberry Pi by default is a normal user.
But Linux also has system administrator users also called Super Users or ‘root’s. In general, we use both terms interchangeably. Administrators basically have permission to perform any action in the system.
During the installation of a Unix system, at least one Super User is created, which normally has the username ‘root’, ‘admin’, ‘administrator’, or ‘superuser’. In Raspbian, the default Super User is ‘root’.
Calling a Super User ‘root’ originates from the fact that they are the users who have access to the root of the system, that is, to /root
Of course, the most critical, important, and dangerous system commands have to be executed by someone with Super User permissions. Super Users, unlike a normal user, can also act on other user accounts.
However, it wouldn’t be very practical if only users logged in as root could execute these tasks. Sometimes it is convenient to grant other users permission to run administrator applications.
But, if we want certain users to be able to run these commands, it would not be very practical to provide them with the root user’s password. It would also not be very practical to have to log out and log back in as root to run the command, having to go back to the directory we were in before, etc. This is where the ‘sudo’ command comes into play.
What is ‘Sudo’?
Sudo (Super User Do) is an application developed in 1980 by Bob Coggeshall and Cliff Spencer, and currently maintained by Todd Miller with the collaboration of Chris Jepeway and Aaron Spangler.
This utility, incorporated in Unix and derived systems (Linux, Mac Os, etc) allows running a command with the privileges of another user. This includes running programs as root, which is the function we will use ‘sudo’ most frequently.
How to use sudo
To run a command with the privileges of another user, we use the following command,
sudo -u anotherUser commandWhere anotherUser is the name of the user we want to emulate, and ‘command’ is the command to be executed.
If we omit the username, which is the most common syntax, we will run the command with root permissions
sudo commandIf you have written a command and realize that you need Super User permissions, you can invoke the last command simply by doing,
sudo !!Another possibility to get Super User permissions would be to use the command
sudo suThis grants us Super User permissions in the session, until we run the command
exitWhich will remove our elevated permissions and return us to our sad existence as a common user. But it is not a good practice to do this and we must get used to doing it only when necessary.
Who can use ‘sudo’
Logically, the control of who can execute the ‘sudo’ application is vital for the security of the system. When running ‘sudo’, the first thing the application does is check in a configuration list that the current user can execute ‘Sudo’.
The ‘sudo’ configuration is saved in the ‘sudoers’ file located in ‘/etc/sudoers’. However, manual editing of the ‘sudoers’ file is strongly discouraged. Instead, we should use the command:
sudo visudo‘visudo’ is an application that allows safe editing of the ‘sudoers’ file. First, it locks the file during editing so that two people do not modify it simultaneously. On the other hand, before saving the ‘sudoers’ file, it checks that the syntax is correct, and stops if it detects any defect.
The ‘sudoers’ file has its own quite particular syntax, and many options to configure. We will only see a brief summary of the many available options.
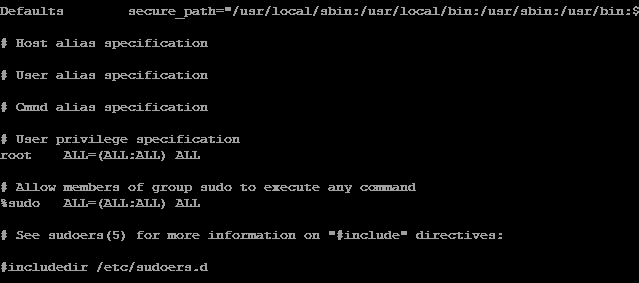
When editing the ‘sudoers’ file you will see that it looks like this:
## User privilege specification
root ALL=(ALL) ALL
suse ALL=(ALL) ALL
pi ALL=(ALL) ALLWhere the simplest syntax of a permission for ‘sudo’ is:
userName ALL=(ALL:ALL) ALLBeing,
- userName indicates the user to which the rule applies
- First ‘All’ indicates that the rule applies to all hosts
- Second ‘All’ indicates that it can run commands as all users
- Third ‘All’ can run commands as all user groups
- Last ‘All’ indicates that it can run all commands
So, for example,
pi ALL=(ALL) NOPASSWD: ALLMeans that the user ‘pi’ can run on all hosts, as any user, any command, and does not have to enter the password.
Of course, there is much more that we could explain about the ‘sudoers’ file, which has many more options and parameters that we can configure. However, it is beyond the scope of this post. If you are more interested, you can consult the program’s documentation.
Alternative way to grant Sudo permissions to a user
Many Linux distributions, such as Raspbian or Ubuntu, come with a group created within the ‘sudoers’ file called ‘sudo’. Any user who remains in this group has the right to execute ‘sudo’.
Therefore, an alternative and perhaps simpler way to give ‘sudo’ permissions to a user is to put them in this group with the following command.
sudo usermod -a -G sudo userNameThe responsibility of the SuperUser
We cannot fail to outline the minimum rules to respect when acting as a root user:
- Respect the privacy of others
- Think before you type
- With great power comes great responsibility
Which is a reminder of the responsibility of being a Super User. First of all, keep in mind that when you mess up there is nothing to protect you from mistakes. You can crash the system all by yourself.
That’s why it is advisable to get used to running commands with elevated permissions only when necessary. The rest of the time work as a ‘normal’ user.
Finally, of course, you should not do anything on others’ accounts that you would not want them to do on yours.
So far the post about users, super users, and the use of the almost essential ‘sudo’ application. From here on we will use ‘sudo’ frequently, and you will soon get used to using it.
In the following posts, we will see user and password management, and user group management, two fundamental aspects to maintain the security of our system.
